 Because you manage a business, we don't have to convince you of the benefits of planning ahead. For example, having an onboarding strategy in place for hiring a new employee will get them acclimated more quickly, which will help them contribute to boosting your bottom line faster. Similarly, planning your IT network maintenances will benefit your organization.
Because you manage a business, we don't have to convince you of the benefits of planning ahead. For example, having an onboarding strategy in place for hiring a new employee will get them acclimated more quickly, which will help them contribute to boosting your bottom line faster. Similarly, planning your IT network maintenances will benefit your organization.
NetWorthy Systems Blog
 It seems odd, but people are declaring 3D printers to be the technology that's going to revolutionize the future while simultaneously moving away from paper printers. Let talk about the printers you use for your business. A print server solution will help you transition away from your current printer setup so that you can take advantage of cool futuristic technologies!
It seems odd, but people are declaring 3D printers to be the technology that's going to revolutionize the future while simultaneously moving away from paper printers. Let talk about the printers you use for your business. A print server solution will help you transition away from your current printer setup so that you can take advantage of cool futuristic technologies!
 Due to the irreplaceable nature of data, server units may be your company's most important assets. Therefore, when it comes time to purchase a new server, you will want to make sure that your new unit will be exactly what your business needs. Getting a model that's too small or too powerful can be costly. Here's what to look for when purchasing a new server.
Due to the irreplaceable nature of data, server units may be your company's most important assets. Therefore, when it comes time to purchase a new server, you will want to make sure that your new unit will be exactly what your business needs. Getting a model that's too small or too powerful can be costly. Here's what to look for when purchasing a new server.
 By now, you have hopefully heard about Windows XP being no longer supported by Microsoft come April, but what you may have missed is that there's another popular Windows OS, Windows Server 2003, that's also set to expire relatively soon. July 14, 2015 is the end of support date for Windows Server 2003. Have you made plans to upgrade?
By now, you have hopefully heard about Windows XP being no longer supported by Microsoft come April, but what you may have missed is that there's another popular Windows OS, Windows Server 2003, that's also set to expire relatively soon. July 14, 2015 is the end of support date for Windows Server 2003. Have you made plans to upgrade?
 Simplifying a complicated procedure is a sure way to get ahead. An enterprise's communication system can be extremely complicated with everything a business needs out of it. Voice over Internet Protocol, aka VoIP, is a solution that can simplify your entire communications system. Simplifying something major like communication will benefit your business in many ways.
Simplifying a complicated procedure is a sure way to get ahead. An enterprise's communication system can be extremely complicated with everything a business needs out of it. Voice over Internet Protocol, aka VoIP, is a solution that can simplify your entire communications system. Simplifying something major like communication will benefit your business in many ways.
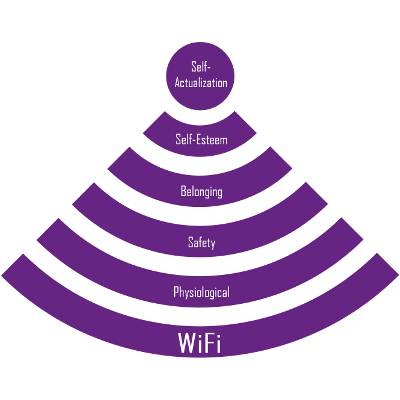 In 1943, psychologist Abraham Maslow published a paper about human motivation that would become the well-known Maslow's Hierarchy of Needs. His theory states that before self-actualization can be achieved, four needs must first be met, like esteem, belonging, safety, and physiological (the most basic which includes, air, food, water, etc.). In 2014, we feel the need to add one more layer to Maslow's pyramid: WiFi.
In 1943, psychologist Abraham Maslow published a paper about human motivation that would become the well-known Maslow's Hierarchy of Needs. His theory states that before self-actualization can be achieved, four needs must first be met, like esteem, belonging, safety, and physiological (the most basic which includes, air, food, water, etc.). In 2014, we feel the need to add one more layer to Maslow's pyramid: WiFi.
 One of the most common ways computer viruses spread is through email. Most of the malware-carrying messages are caught in your account's spam filter, so you don't have to worry about those. It's the malicious emails that make it to your inbox that you need to be mindful of, and phishing emails are by far the most dangerous.
One of the most common ways computer viruses spread is through email. Most of the malware-carrying messages are caught in your account's spam filter, so you don't have to worry about those. It's the malicious emails that make it to your inbox that you need to be mindful of, and phishing emails are by far the most dangerous.
 It's good to backup your data, but can you have too much of a good thing? While this may be the case for several enjoyable activities like partying and buffets, this isn't the case with data backup. In fact, the more layers of data backup you have, the more secure you will be. How good is your data backup solution?
It's good to backup your data, but can you have too much of a good thing? While this may be the case for several enjoyable activities like partying and buffets, this isn't the case with data backup. In fact, the more layers of data backup you have, the more secure you will be. How good is your data backup solution?
 One of the purposes of technology is to help your business grow. The best way to achieve this goal is to be intentional with your technology. Sometimes running a business can be so hectic that keeping up with your technology becomes an afterthought. Neglecting your technology can eat into your organization's profits; therefore, it makes more sense to outsource your IT.
One of the purposes of technology is to help your business grow. The best way to achieve this goal is to be intentional with your technology. Sometimes running a business can be so hectic that keeping up with your technology becomes an afterthought. Neglecting your technology can eat into your organization's profits; therefore, it makes more sense to outsource your IT.
 Remember back when buying mobile devices for your business meant choosing between a handful of laptops? Thanks to the increased proliferation of devices like smartphones, tablets, netbooks, and the development new hybrid models, it's become quite the task to pick out the right make and model. Here are five questions to consider when picking out mobile devices for your organization.
Remember back when buying mobile devices for your business meant choosing between a handful of laptops? Thanks to the increased proliferation of devices like smartphones, tablets, netbooks, and the development new hybrid models, it's become quite the task to pick out the right make and model. Here are five questions to consider when picking out mobile devices for your organization.
 If you've never taken advantage of remote support to remedy an IT problem, then you're likely doing IT support the hard way by having a technician physically take care of every issue. While it's always nice to chat with your friendly tech, you may be able to save yourself a whole lot of time and money by taking care of the issue with remote support.
If you've never taken advantage of remote support to remedy an IT problem, then you're likely doing IT support the hard way by having a technician physically take care of every issue. While it's always nice to chat with your friendly tech, you may be able to save yourself a whole lot of time and money by taking care of the issue with remote support.
 Working in the IT industry means embracing change and the latest technology trends. Doing the same thing day-in and day-out is a luxury we don't have, and frankly, sounds kind of boring. Since computers were first invented, there's been a need to service them. Here's a look at how the IT service industry has changed over the past 50 years.
Working in the IT industry means embracing change and the latest technology trends. Doing the same thing day-in and day-out is a luxury we don't have, and frankly, sounds kind of boring. Since computers were first invented, there's been a need to service them. Here's a look at how the IT service industry has changed over the past 50 years.
 You may feel like your computer network is immune to data loss, but according to a study by Blackblaze.com, 46% of users experience data loss every year. Whether it's from something big like a natural disaster, or minor like improperly removing a flash drive, every form of data loss is costly and can be prevented with a data backup plan.
You may feel like your computer network is immune to data loss, but according to a study by Blackblaze.com, 46% of users experience data loss every year. Whether it's from something big like a natural disaster, or minor like improperly removing a flash drive, every form of data loss is costly and can be prevented with a data backup plan.
 It's nice to get a shiny new computer that's fast, powerful, and has all the latest features. Before you install your new machine, you have to make a decision about what to do with your old one. Your old computer has been a faithful friend over the years so you may feel bad pitching it to the curb; instead, consider giving it a new home.
It's nice to get a shiny new computer that's fast, powerful, and has all the latest features. Before you install your new machine, you have to make a decision about what to do with your old one. Your old computer has been a faithful friend over the years so you may feel bad pitching it to the curb; instead, consider giving it a new home.
 At a recent security event, VP of Gartner Neil MacDonald broke down the fundamentals of IT security into four categories, "Information security was never about device lockdown, or dictating applications, or building firewalls. It was always about protecting the confidentiality, the integrity, the authenticity, the availability of information." Here's a closer look at these four security qualities.
At a recent security event, VP of Gartner Neil MacDonald broke down the fundamentals of IT security into four categories, "Information security was never about device lockdown, or dictating applications, or building firewalls. It was always about protecting the confidentiality, the integrity, the authenticity, the availability of information." Here's a closer look at these four security qualities.
 The world you do business in is a pretty dangerous and messed up place, and things always seem to be getting worse. Thankfully, security technology is improving, which helps offset the risks of living in a perilous world. You can take advantage of these security improvements by installing intelligent surveillance cameras for your business.
The world you do business in is a pretty dangerous and messed up place, and things always seem to be getting worse. Thankfully, security technology is improving, which helps offset the risks of living in a perilous world. You can take advantage of these security improvements by installing intelligent surveillance cameras for your business.
 Your company's technology infrastructure is made up of several complex systems that all work together in order to keep your business running smoothly. Your IT infrastructure functions much in the same way as another type of infrastructure, your house. It's surprising how much you can learn about computer networking by looking at "This Old House."
Your company's technology infrastructure is made up of several complex systems that all work together in order to keep your business running smoothly. Your IT infrastructure functions much in the same way as another type of infrastructure, your house. It's surprising how much you can learn about computer networking by looking at "This Old House."
 We are in a unique time of Windows OS transitions. The redesigned Windows 8 has been out for one year, and the first major update to it (Windows 8.1) was just released. Additionally, the popular Windows XP expires in April, forcing everybody to upgrade and choose between Windows 7 and 8. Which OS will your business go with?
We are in a unique time of Windows OS transitions. The redesigned Windows 8 has been out for one year, and the first major update to it (Windows 8.1) was just released. Additionally, the popular Windows XP expires in April, forcing everybody to upgrade and choose between Windows 7 and 8. Which OS will your business go with?
 What would happen if your business experienced a disaster and your sensitive information was erased? If you don't have a business continuity plan in place that includes data backup and recovery, then it's highly unlikely your company will survive. To protect your business, you will want to consider and choose one of these three backup solutions.
What would happen if your business experienced a disaster and your sensitive information was erased? If you don't have a business continuity plan in place that includes data backup and recovery, then it's highly unlikely your company will survive. To protect your business, you will want to consider and choose one of these three backup solutions.
 You can connect to over 2.7 billion people over the Internet, but you probably shouldn't. There are many people on the Internet with bad intentions, along with several websites that can harm your business. With a Unified Threat Management (UTM) tool, you can protect your business by filtering out the worst of the web.
You can connect to over 2.7 billion people over the Internet, but you probably shouldn't. There are many people on the Internet with bad intentions, along with several websites that can harm your business. With a Unified Threat Management (UTM) tool, you can protect your business by filtering out the worst of the web.