Have any question?
Call (409) 861-4450
Call (409) 861-4450
 It’s natural to replace older technologies with better, more recent models. However, the future isn’t looking too bright for the world’s most common website encryption method, SHA1, which will soon be replaced by a more secure protocol. Pretty soon, browsers and devices may have some difficulty reading the latest security certificates, which could cause quite a problem if it’s not remedied.
It’s natural to replace older technologies with better, more recent models. However, the future isn’t looking too bright for the world’s most common website encryption method, SHA1, which will soon be replaced by a more secure protocol. Pretty soon, browsers and devices may have some difficulty reading the latest security certificates, which could cause quite a problem if it’s not remedied.
 One of the most masterful arts of deception that hackers use is the phishing attack, which attempts steal sensitive credentials from unwary victims. The anonymity afforded to criminals on the Internet is what makes this possible. Using phishing attacks, hackers attempt to steal credentials or personal records by forging their identities. What’s the best way to protect your business from these attacks?
One of the most masterful arts of deception that hackers use is the phishing attack, which attempts steal sensitive credentials from unwary victims. The anonymity afforded to criminals on the Internet is what makes this possible. Using phishing attacks, hackers attempt to steal credentials or personal records by forging their identities. What’s the best way to protect your business from these attacks?
 A good business practices extreme caution when using the Internet, thanks to hackers using any means possible to unleash threats against organizations of all sizes. You teach your employees how to avoid threats and to avoid suspicious websites, but what if that’s not enough to keep hackers out of your network infrastructure?
A good business practices extreme caution when using the Internet, thanks to hackers using any means possible to unleash threats against organizations of all sizes. You teach your employees how to avoid threats and to avoid suspicious websites, but what if that’s not enough to keep hackers out of your network infrastructure?
 Security is a top priority in today’s business environment, especially following high-profile hacks of notable enterprises. Unfortunately, the fact of the matter is that these hacks could have been prevented if both the employees and employers of these organizations followed strict security best practices for their technology. Thankfully, it doesn’t have to be hard to teach your team how to properly use technology.
Security is a top priority in today’s business environment, especially following high-profile hacks of notable enterprises. Unfortunately, the fact of the matter is that these hacks could have been prevented if both the employees and employers of these organizations followed strict security best practices for their technology. Thankfully, it doesn’t have to be hard to teach your team how to properly use technology.
 Businesses are embracing the cloud model as the accepted form of computing, but some are finding that they want more control over their data. When you use a public cloud, you’re relinquishing some control so that you don’t have to deal with network security and hosting. If you’re serious about protecting your data and maintaining the infrastructure yourself, there are several benefits of operating your own private cloud infrastructure.
Businesses are embracing the cloud model as the accepted form of computing, but some are finding that they want more control over their data. When you use a public cloud, you’re relinquishing some control so that you don’t have to deal with network security and hosting. If you’re serious about protecting your data and maintaining the infrastructure yourself, there are several benefits of operating your own private cloud infrastructure.
 As a business owner, you’re constantly moving around. At the same time, you’re expected to keep in touch with your base of operations, respond to employee and client inquiries, and many more mission-critical tasks that require the use of remote technology solutions. Unfortunately, public WiFi hotspots are known to be cesspools of online filth, where a secure connection is nothing but a dream. One way to correct this issue is with a Virtual Private Network (VPN).
As a business owner, you’re constantly moving around. At the same time, you’re expected to keep in touch with your base of operations, respond to employee and client inquiries, and many more mission-critical tasks that require the use of remote technology solutions. Unfortunately, public WiFi hotspots are known to be cesspools of online filth, where a secure connection is nothing but a dream. One way to correct this issue is with a Virtual Private Network (VPN).
 It seems like we can’t go on the Internet without reading about some sort of data breach. Sometimes they’re caused by poor security measures, like lack of data encryption or two-factor authentication; other times, it’s because of lackluster password security. Despite the antiquity of the username and password, they’re staples in the modern office. Thus, it’s important that they’re as secure as possible at all times.
It seems like we can’t go on the Internet without reading about some sort of data breach. Sometimes they’re caused by poor security measures, like lack of data encryption or two-factor authentication; other times, it’s because of lackluster password security. Despite the antiquity of the username and password, they’re staples in the modern office. Thus, it’s important that they’re as secure as possible at all times.
 When a company is lax about their network security, this can lead to countless threats swarming the network and invading your systems. Yet, sometimes the most dangerous threats come from within. A common issue comes from employees accessing undisclosed files unintentionally and deleting them, which can cause more damage than you think.
When a company is lax about their network security, this can lead to countless threats swarming the network and invading your systems. Yet, sometimes the most dangerous threats come from within. A common issue comes from employees accessing undisclosed files unintentionally and deleting them, which can cause more damage than you think.
 A trend that’s taking the office by storm is BYOD, or Bring Your Own Device. These policies entail workers bringing their own devices to the office and using them for work-related purposes. While this opens up many avenues for enhanced productivity and efficiency, being too laissez faire with your BYOD policy could instigate some problems later on, primarily in the security field.
A trend that’s taking the office by storm is BYOD, or Bring Your Own Device. These policies entail workers bringing their own devices to the office and using them for work-related purposes. While this opens up many avenues for enhanced productivity and efficiency, being too laissez faire with your BYOD policy could instigate some problems later on, primarily in the security field.
 We always talk about protecting your computers and servers from outside threats, but what about protecting your smartphones? There isn’t much difference between a smartphone and a computer. They both function in very similar ways with access to a variety of apps, social media, and browsers. Your smartphone could hold much more valuable data than just contacts or text messages.
We always talk about protecting your computers and servers from outside threats, but what about protecting your smartphones? There isn’t much difference between a smartphone and a computer. They both function in very similar ways with access to a variety of apps, social media, and browsers. Your smartphone could hold much more valuable data than just contacts or text messages.
 Changing your password is a pain. After you’ve gone several months with the same one, it can be difficult to remember your new password. Despite this, it’s always recommended that you change your passwords often. Unfortunately, when you change all of your passwords often, it’s even easier to forget them. Instead of using a post-it note on your monitor, you should instead try using a password manager.
Changing your password is a pain. After you’ve gone several months with the same one, it can be difficult to remember your new password. Despite this, it’s always recommended that you change your passwords often. Unfortunately, when you change all of your passwords often, it’s even easier to forget them. Instead of using a post-it note on your monitor, you should instead try using a password manager.
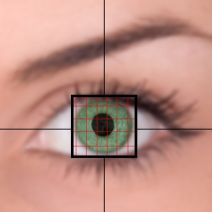 Humans are always trying to improve security protocols that can protect against increasingly advanced online threats. Unfortunately, the threats only grow stronger in response, and the war against malicious online activity rages on. Biometrics are security measures that are growing in popularity, but are expensive and difficult to integrate. Now, the US military is funding a campaign to make it more readily available to end users.
Humans are always trying to improve security protocols that can protect against increasingly advanced online threats. Unfortunately, the threats only grow stronger in response, and the war against malicious online activity rages on. Biometrics are security measures that are growing in popularity, but are expensive and difficult to integrate. Now, the US military is funding a campaign to make it more readily available to end users.
 One would assume that software preinstalled on a new PC is secure and has been properly vetted by the manufacturer. This is the case 99 percent of the time, but an exception has recently been discovered with the Superfish app, which came installed on new Lenovo computers sold between September and December of 2014. How can you protect your PC from this fishy security threat?
One would assume that software preinstalled on a new PC is secure and has been properly vetted by the manufacturer. This is the case 99 percent of the time, but an exception has recently been discovered with the Superfish app, which came installed on new Lenovo computers sold between September and December of 2014. How can you protect your PC from this fishy security threat?
 When the Internet was first established, malware and hacking were in their infancy, and not as much of an immediate problem as they are today. Thanks to this fact, the Internet wasn’t really created with a certain security design in mind, and has instead adapted to shifts in its environment. Unfortunately, as hackers grow more powerful, several of these patchwork protocols are growing outdated.
When the Internet was first established, malware and hacking were in their infancy, and not as much of an immediate problem as they are today. Thanks to this fact, the Internet wasn’t really created with a certain security design in mind, and has instead adapted to shifts in its environment. Unfortunately, as hackers grow more powerful, several of these patchwork protocols are growing outdated.
 With the Internet of Things fast approaching, and BYOD becoming prevalent in the business world, there are a lot more devices connecting to wireless networks now than at any time in history. This makes new technology far more mobile, but it also means that more threats are able to access networks from countless new entry points. These threats can access your business’s devices which contain sensitive corporate data. How can you protect your devices from this wave of new threats?
With the Internet of Things fast approaching, and BYOD becoming prevalent in the business world, there are a lot more devices connecting to wireless networks now than at any time in history. This makes new technology far more mobile, but it also means that more threats are able to access networks from countless new entry points. These threats can access your business’s devices which contain sensitive corporate data. How can you protect your devices from this wave of new threats?
 Email has revolutionized the way we communicate, but in some cases it can be a dangerous distraction to productivity. This is especially true if your company is trying to maintain its own Exchange mail server. Does having email on the brain give you a headache? If so, you might consider looking into our hosted email Exchange solution.
Email has revolutionized the way we communicate, but in some cases it can be a dangerous distraction to productivity. This is especially true if your company is trying to maintain its own Exchange mail server. Does having email on the brain give you a headache? If so, you might consider looking into our hosted email Exchange solution.
 Cloud computing has taken the business world by storm, but despite this, some entrepreneurs aren’t so convinced that migrating their data to the cloud is a good idea. These business owners usually make this decision based off of misconceptions surrounding the cloud, which might be preventing them from making full use of it. Here are two of the most common misconceptions surrounding the cloud.
Cloud computing has taken the business world by storm, but despite this, some entrepreneurs aren’t so convinced that migrating their data to the cloud is a good idea. These business owners usually make this decision based off of misconceptions surrounding the cloud, which might be preventing them from making full use of it. Here are two of the most common misconceptions surrounding the cloud.
Get the Knowledge You Need to Make IT Decisions
Technology is constantly evolving, and keeping up can feel overwhelming. Whether you want to understand cybersecurity threats, explore automation, or learn how regulations like PCI DSS impact your business, we’ve made it easy to access clear, straightforward insights on key IT topics.
Learn more about what NetWorthy Systems can do for your business.
NetWorthy Systems
701 W. Division Ave Suite 100
Orange, Texas 77630